"Yesterday, Joomla! 3.6.4 was released, patching a critical privilege escalation and arbitrary account creation vulnerability.
As we’ve seen some exploits attempts occurring in the wild, we feel it is a good time to describe what the issue is and how it was fixed.
"
Analyzing the Patch
It was fairly easy to figure out where the vulnerable code was, as pretty much all the patch does (with the exception of fixing an additional two factor authentication bug) is basically remove the register method from the UsersControllerUser class. So that’s where our investigation started.
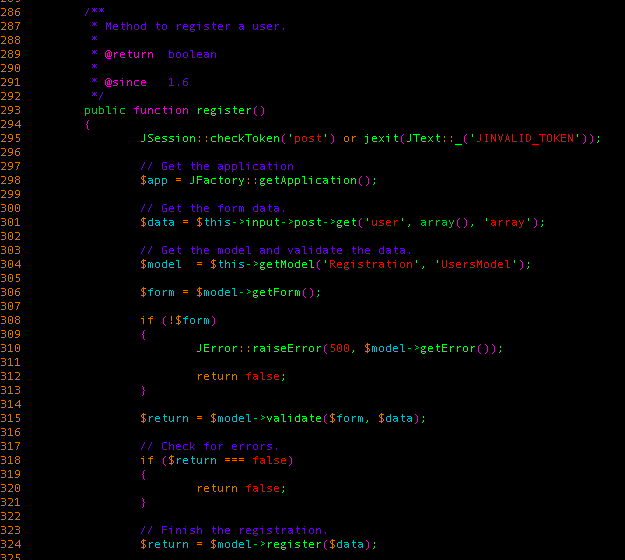
All in all, what this method does is it takes user input from the user POST parameter (which is intended to be an associative array) and validates whether specific parameters are properly formatted (email address, username, etc.). If it’s all good, it pushes the array to the register method from the UsersModelRegistration class.
'via Blog this'
3 comments:
Thanks for sharing informative content about the Joomla.
Top Web Design Companies in Bangalore
Thanks for the useful information and amazing post
Top Web and Mobile Development Company In Bangalore
Thank you for the information.
For comprehensive network protection, look no further than Indian Cyber Security Solutions. As a leading NPT service provider in India, ICSS offers thorough and expert network penetration testing to identify and address potential vulnerabilities. Their dedicated approach ensures your network is secure against evolving threats, providing peace of mind for your organization.
Post a Comment